Manage and control access to your critical audit/log information in cloud-based applications, Internet of Things (IoT) lightweight systems, and mobile distributed apps.
The Security Software Logger/Browser design uses a Secure Vault, Protected RAM and Output Storage to securely protect critical and sensitive audit/log information during the development, integration, and deployment of applications.
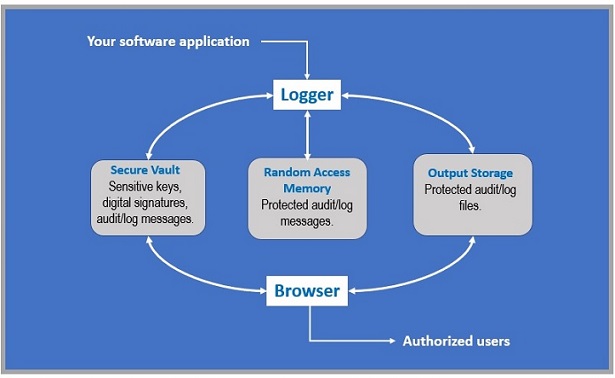
Regardless where your application resides (in the cloud, IoT, mobile or enterprise computing environment) the Security Software Logger/Browser provides:
- Application Programming Interface functions that allow your software applications to protect audit/log messages.
- A Secure Vault to protect software application audit/log messages during source code development.
- The Logger that protects audit/log messages while stored in RAM and in Output Storage.
- The Browser that allows only authorized users to view protected audit/log messages.
The Security Software Logger/Browser configuration and operational flexibility allows:
- Scalability from small computing environments to large complex systems.
- Robust and secure validation to ensure reliable execution.
- Lightweight runtime for improved execution performance.
- Separation of duties between logging messages and viewing audit/log messages.
